Why and how do websites get hacked?
5 min read

The majority of mainstream services and software applications are at some point the target of unwanted attention from hackers, denial of service attackers or geeky glory hunters, and unfortunately, regardless of how much you invest in website security, total security remains an unobtainable target.
Whilst major software vendors like Microsoft and high security facilities like the Whitehouse and NHS are still susceptible to attacks, what chance do small website owners have?

Content management systems
Due to its own success, WordPress bears the brunt of the attention in the CMS world because it’s the largest and most popular platform with 65% market share. Added to this is the Open Source nature of WordPress, which means its underlying code is more easily scrutinised and vulnerabilities exposed.
Before websites used content management systems, attacks were less commonplace although they did occur, but websites are powered by CMS’s and therefore database-driven now, providing more potential to exploit weak points and opportunity to cause damage.
It’s not just WordPress which suffers, the other CMS platforms get plenty of unwanted attention too, taking a look at vendors release notes paints a clear picture of the required frequency of website security patches to plug gaps and constantly need to improve security:
- https://codex.wordpress.org/Current_events
- https://devnet.kentico.com/download/hotfixes
- https://www.drupal.org/project/drupal/releases
- https://docs.joomla.org/Category:Version_History
- https://devdocs.magento.com/guides/v2.3/release-notes/bk-release-notes.html
- https://www.concrete5.org/about/blog/core-releases
- https://docs.microsoft.com/en-us/officeupdates/sharepoint-updates
- https://typo3.org/cms/roadmap/typo3-8-release-notes/
Is WordPress secure?
WordPress itself is very secure as long as security best practices are followed. The main cause of WordPress sites being compromised is out of date plugins. Some of the most basic security techniques include:
- Remove the default user ‘admin’
- Use complex password policies and change them regularly
- Keep WordPress core and all plugins up to date
- Use a reputable website host, avoid the cheapest shared hosting packages
- Ensure that the default database table prefix is changed from wp_
There are many more best-practice security measures which we implement on our clients WordPress websites, and the landscape is constantly changing so it’s really important to keep a careful watch out for new ways to improve website security and performance.
Types of attackers
Ethical hackers known as white-hat hackers, could be for example security researchers or paid and trained experts, who break security for non-malicious reasons, such as testing their own security system, performing penetration tests or vulnerability assessments for a client.
They would be expected to notify the vendor once a vulnerability is detected and help to make sure the holes are patched.
Cybercriminals or black-hat hackers violate computer security for personal gain, using their expertise to find or develop software holes and break into secure networks to destroy, modify, or steal data; or to make the network unusable for those who are authorised to use the network.
They also work to sell information about the security holes, zero-day vulnerabilities and exploits to other criminals for use.
Hackers could also be disgruntled employees, individuals or small groups often referred to as hacktivists, competitors in particularly competitive market places who are happy to cross the legal line to gain a competitive advantage, terrorists or even intelligence services or governments.
Bots
Although it is possible for your website or organisation to be a direct target, especially if you’re involved in a controversial activity or subject, it is more likely that an unidentifiable robot has crawled the web looking for sites with known vulnerabilities, for example, an out of date CMS application or plugin.
The bot developers motivations range from ‘just because they can’, ’to see if they could’, or to achieve geek fame by hitting the headlines as the brains behind a major security breach. The latter having in the past resulted in lucrative employment opportunities to help improve security. Ironic.

Commercial gain
Attacks can sometimes be for commercial gain, including these examples which we have experienced before:
- Visually changing a website to promote another product or service, usually something unsavoury, illegal or controversial
- Embedding hidden links in a site which provide valuable back-links to another site to help organic search performance
- Redirecting traffic to another website, often an online shop
- A denial of service attack which stops a website or server from being used
- File distribution, so using a site to distribute other content
- Data theft.
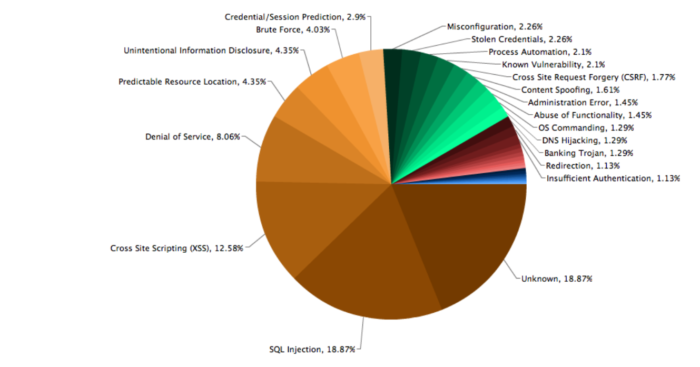
In the pie-chart below created from Web Hacking Incident Database (WHID) clearly shows that whilst many different attack methods exist, SQL injection and XSS are the most popular.
Many other attack methods, such as Information Disclosures, Content Spoofing and Stolen Credentials could all be side-effects of an XSS attack – source https://medium.com/wordpress-hacked-help/10-web-hacking-techniques-you-must-know-about-in-2017-1ff9d78d9669
Mitigation
CDN’s
Content Delivery Networks offer many benefits including performance optimisation, load balancing and fast global delivery, plus greatly improved security using built-in WAF’s (Web Application Firewalls) to block known bad traffic from connecting to you site. The best CDN services are provided by:
- Cloudflare
- Cloudfront by Amazon for use on AWS
- Incapsula
- And other reputable solutions can be seen at https://www.cdnplanet.com/
WAF’s
Implementing a Website Application Firewall provides a great level of protection against threats to your website. We recommend the following solutions:
- Sucuri – free and premium versions available including a great WordPress plugin
- Wordfence -free and premium versions available including a great WordPress plugin
- Defender
Granite 5 sitecare service
We provide a comprehensive level of support and after-sales service to protect your online brand and digital presence, offering peace of mind to our clients that their websites are maintained, proactively supported and carefully monitored 24/7.
Our team of digital specialists pride ourselves on providing excellent customer services and effective digital marketing, both of which can only be achieved with exceptional reliability and rapid response in the event of unforeseen problems.
Technical support is required for all websites and hosted applications to ensure maximum security and performance is maintained. Technical support is defined as bugs or technical issues which affect the normal operation of the site or service in line with the agreed specification.
We offer guaranteed response rates, typically 0.5 days for complete loss of service, 1 working day for significant service interruption, for example, a core feature not working, and 3 working days for minor loss of service.
Backup and monitoring
A 24/7 monitoring service provided by Uptime Robot allows us to respond quickly if outages do occur, and separate server monitoring alerts us when resources hit 60% utilisation so gives us advance warnings of problems.
We have a robust backup strategy which includes offsite daily incremental backups, this is for peace of mind and we can usually restore within 30 minutes (depending upon the size of the site).
